Division of Dockets Management (HFA‐305)
Center for Devices and Radiological Health
Food and Drug Administration
5630 Fishers Lane
Rockville, MD 20852
September 22, 2021
Ref: Strengthening Cybersecurity Practices Associated with Servicing of Medical Devices: Challenges and Opportunities
Docket No. FDA-2021-N-0561
Dear Sir/Madam:
This is to submit comments to the discussion paper reference above.
I. Introduction of Alliance
Before providing information and comments, please allow us to introduce the Alliance for Quality Medical Device Servicing (the “Alliance”). The Alliance is an informal coalition of seven leading independent medical device service organizations which support healthcare delivery organization (“HDOs”) across the United States, namely TRIMEDX, Sodexo, Crothall, ABM, Agiliti, the InterMed Group, and TKA.
Alliance members collectively employ tens of thousands of associates across all fifty states and actively service and maintain millions of medical devices. The Alliance members, as independent service organizations (“ISOs”), offer to their HDO client not only safe and effective service, but also an equipment agnostic perspective focused on ensuring safety, reliability, and efficiency.
The Alliance’s mission is to advance policy solutions that will result in ensuring the safety and availability of medical devices for hospitals and lowering health care costs nationwide. The Alliance is working to continue to make ISOs a cost-effective solution for providers, which ultimately improves the quality of patient care.
II. General Comments
The Alliance applauds FDA’s initiative in discussing cybersecurity issues that are unique to the servicing of medical devices and seeking input from stakeholders on the challenges and opportunities.
We agree that cybersecurity is a major issue that affects the safety and wellbeing of all Americans. The COVID-19 pandemic has clearly shown the critical nature of medical devices and the recent ransomware attacks have brought to the forefront the need to protect the healthcare infrastructure. We also agree that this is a shared responsibility of all stakeholders, including OEMs, HDOs (including their clinical users and their IT and in-house servicing teams), and ISOs. Finally, we also agree that all servicers—regardless of whether employed by OEMs, not only when servicing the devices they produced but also when servicing devices manufactured by other OEMS (aka multi-vendor service – MVS), HDOs or ISOs—have an important role in identifying cyber exploits and vulnerabilities and in participating in the prevention and mitigation efforts.
Above all, as explained below in detail, we fully agree with your statement that “FDA is not suggesting that devices be secured to prevent non-OEM servicing when such servicing is technically feasible and appropriate.” Without strict oversight from the FDA, the “privileged access” could become a broad and uncontrollable excuse for OEMs to monopolize device servicing and severely restrict the viability of non-OEM servicing, which FDA recognized in its 2018 FDARA 710 report “… is critical to the functioning of the U.S. healthcare system.” Furthermore, such anticompetitive action also violates President Biden’s Executive Order on Promoting Competition in the American Economy1.
III. Answers to FDA Discussion Questions
Instead of commenting on each of the 4 areas identified by FDA and then answering the discussion questions, please allow us to include our comments on those areas within our answers to the questions so as to avoid repetition.
- What are the cybersecurity challenges and opportunities associated with the servicing of medical devices?
First, in almost every healthcare facility the servicers (heretofore including those employed by HDOs, OEMs, third parties, or ISOs) are the ones who gather and provide critical device information (e.g., IP & MAC addresses, ports, wireless and wired network, system and anti-virus software revision levels, etc.) to the HDO’s IT cybersecurity team. These cybersecurity functions have a wide range of sophistication, size, and scope based on the needs of the organization, thereby limiting a “one size fits all” approach. Next, the servicers are responsible for installing validated software updates and patches as directed by OEMs whenever, and if, issued. It is worth noting that we recognize and understand that it is the OEMs responsibility, solely, to assess the risks and determine the appropriate remediations for the devices they produced. Should a design change, such as a patch, be required, the OEM is also solely responsible for developing and validating said solution. Unfortunately, it is not uncommon for OEMs to be slow or even fail to provide remediation for many vulnerabilities (e.g., WannaCry). Finally, the servicers are those who are likely to uncover vulnerabilities and/or device failures caused by malware when performing scheduled or unscheduled maintenance.
The two main challenges servicers are currently facing and will continue to face in addressing cybersecurity are:
a) Privileged Access: Almost all the activities mentioned above require “privileged access” to the devices. Without such access, it will not only be impossible to participate and assist in the cybersecurity efforts but also severely limit the servicers’ ability to maintain devices. This could lead to not only unsafe and out of specification devices but also to delays or diversions of care, putting patients’ lives at additional risk. We urge FDA to explicitly mandate OEMs to provide privileged access to device owners and servicers, e.g., by revising the “Postmarket Management of Cybersecurity in Medical Devices – Guidance for Industry and Food and Drug Administration Staff” document.
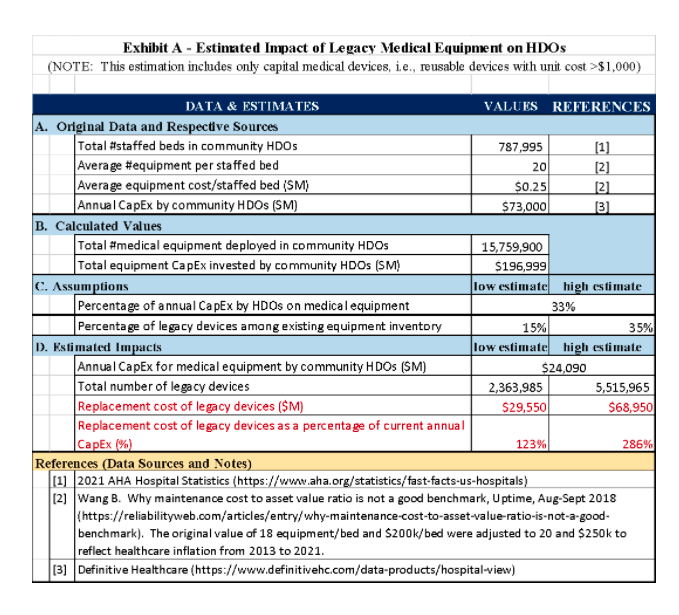
b) Legacy Devices: As mentioned in the Discussion Paper, there is a large amount of legacy devices that are working well and are essential for the care of patients in almost all HDOS, “particularly in rural and underserved communities” as stated by FDA. The amount of legacy devices is grossly estimated in the order of 2.4 – 5.5 million pieces and the replacement cost in the range of $30 – 70 B, which is more than what is currently spent each year by all American community (non-governmental) hospitals—roughly $24 B (see Exhibit A). While there are some mitigation tools available, some of these legacy devices could potentially pose a significant threat to public health (see CISA’s ICE-CERT Advisories2). Furthermore, sometimes there is no safer replacement device available on the market yet. We urge FDA to encourage OEMs and HDOs to develop a more gradual phasing out of these devices over a period of time that is feasible for the HDOs.
As mentioned above, one of the opportunities for servicers to contribute to cybersecurity is to detect and provide early warning on vulnerabilities and breaches that are yet unknown to some others device owners. In addition, servicers can verify the effectiveness of the remediation and mitigation efforts (software updates and patches, network segmentation, etc.). However, for these opportunities to become fully useful for the rest of the nation, a centralized Information Sharing and Analysis Organizations (ISAOs) mentioned in the Discussion Paper must materialize very soon. We urge the FDA to establish a single centralized and neutral clearinghouse to collect, analyze and distribute vulnerabilities and mitigations so every HDO and respective servicer do not have to “reinvent the wheel.”
2. Are the four areas identified in this discussion paper (privileged access, identification of cybersecurity vulnerabilities and incidents, prevention and mitigation of cybersecurity vulnerabilities, and product lifecycle challenges and opportunities) the correct cybersecurity priority issues to address in the servicing of medical devices? If not, which areas should be the focus?
While we agree that the four areas identified in the discussion paper are the priority issues that need to be addressed, we believe this discussion needs to include other stakeholders, especially the HDOs and healthcare professionals. After all, medical devices are nothing but a tool for them to provide health care and save lives as eloquently explained by a Massachusetts General Hospital’s ICU medical director in the preeminent medical journal The Lancet3.
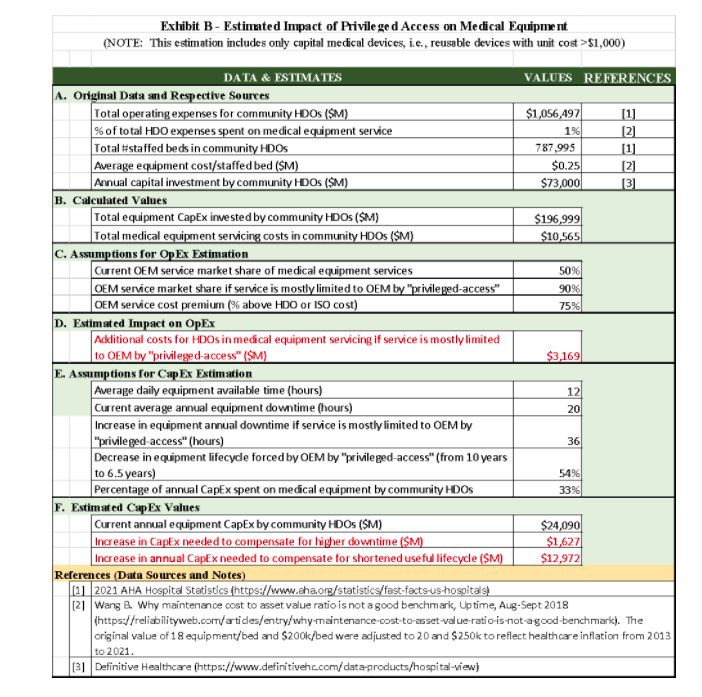
Without the buy-in and active participation of HDO staff, it is virtually impossible to ensure cybersecurity. It is also essential to bring to the table HDO executive leadership, as cybersecurity possesses significant challenges to HDOs in terms of their financial viability in both operational expenses and capital expenditure, in addition to the replacement of legacy devices mentioned above, as the estimates below show (please see details in Exhibit B):
a) Operational Expenses (OpEx): If servicing becomes limited only to the OEMs due to the privileged-access excuse, HDOs and ISOs will have to rely mostly on OEM services instead of in-house teams and ISOs. The resulting additional cost is likely to be in the ballpark of $3 B/year, which would be near 30% of the current total equipment servicing market (around $10 B/year4).
b) Capital Expenditure (CapEx): two types of CapEx are likely to be required if OEMs are allowed to strictly limit privileged access: (i) additional equipment required to compensate for the delay caused by the travel and availability of OEM service representatives and (ii) shortened product lifecycle forced by OEMs. The first CapEx can be estimated to be at least $1.6 M for all HDOs (except for those belonging to the government), while the second one could be an increase of about 54% of current annual CapEx, i.e., an additional about $13 B per year.
Incidentally, the “responsibility agreements” mentioned in the discussion paper are good tools in principle but it is unclear whether in practice it can work as well as intended. Some of the OEMs may no longer be in business even if their products are not actually legacy devices. While many OEMs may be willing to sign such agreements when selling new equipment, they may not be so willing to do so a few years after the sale alleging “end of support.”
In essence, we urge the FDA to also engage the trade associations of the HDOs and healthcare professionals, e.g., the American Hospital Association (AHA), Federation of American Hospitals (FAH), and American Medical Association (AMA) on this subject as their members are the primary users of medical devices, not the servicers.
3. How can entities that service medical devices contribute to strengthening the cybersecurity of medical devices?
While the Alliance cannot speak for all servicing entities and individuals—regardless of whether employed by HDOs, OEMs or ISOs—we believe most, if not all, are willing to contribute to strengthening the cybersecurity of medical devices. They understand that their businesses, jobs, and careers are at jeopardy if this issue is not properly addressed. Furthermore, we all appreciate that cyberattacks can affect the lives and well-being of the American people, including ourselves.
As mentioned above, the servicers are the frontline workers in medical device cybersecurity. They help build the cybersecurity infrastructure, identify and report vulnerabilities, install the software updates and patches, and verify the effectiveness of the prevention and mitigation efforts. Their dedication and commitment to the patients and healthcare workers have been widely and deeply proven in this COVID-19 pandemic, even when some OEMs declined to provide service information, replacement parts and/or keys for privileged access to software5. We are seriously concerned that without proper and strict oversight from FDA, the servicing entities and individuals could become disillusioned with the lack of support for their activities and decide to abandon their businesses and careers, thus, putting the American health system and public at jeopardy. In fact, the industry is already struggling—like many others are—in recruiting new employees to counter the impact of an aging workforce6. Therefore, we urge the FDA to assert leadership in medical device cybersecurity and reassure servicing entities and individuals by establishing clear responsibilities of each of the stakeholders and appropriate consequences in case of violation.
IV. Conclusions
Again, the Alliance would like to commend the FDA for its efforts in addressing medical device cybersecurity.
As FDA stated in the discussion paper, this is a shared responsibility of all stakeholders, including OEMs, HDOs, servicers, healthcare professionals, and government agencies. The challenges and opportunities transcend well beyond the OEMs and servicers. As we pointed out above, while the servicers can help and will likely have to shoulder additional burdens, the American health system—and thus the American public—is ultimately the one that will be directly and seriously impacted. Furthermore, as a hearing of the U.S. House of Representatives’ Subcommittee on Oversight and Investigations of the Committee on Energy and Commerce revealed, HDOs are unprepared to respond to ransomware attacks7. Therefore, we urge FDA to broaden the discussion with all the stakeholders, especially the HDOs, healthcare professional associations, and other federal agencies like the Centers for Medicare & Medicaid Services (CMS), the Veterans Health Administration, and the Department of Defense (because of its military hospitals).
We remain interested and available to participate and contribute to securing medical devices against cyberattacks.
Sincerely yours,
The Alliance for Quality Medical Device Servicing
1. https://www.whitehouse.gov/briefing-room/presidential-actions/2021/07/09/executive-order-on-promoting-competition-in-the-american-economy/
2. https://us-cert.cisa.gov/ics/advisories
3. https://www.thelancet.com/action/showPdf?pii=S0140-6736%2821%2900445-1
4. See, e.g., https://www.grandviewresearch.com/industry-analysis/medical-equipment-maintenance-market and https://www.lucintel.com/medical-equipment-maintenance-market.aspx
5. http://protomag.com/articles/who-has-right-repair-medical-equipment
6. See, e.g., https://24x7mag.com/professional-development/department-management/succession-planning/plan-now-next-htm-generation/
7. See https://energycommerce.house.gov/sites/democrats.energycommerce.house.gov/files/documents/Witness%20Testimony_Dameff_OI_2021.07.20.pdf